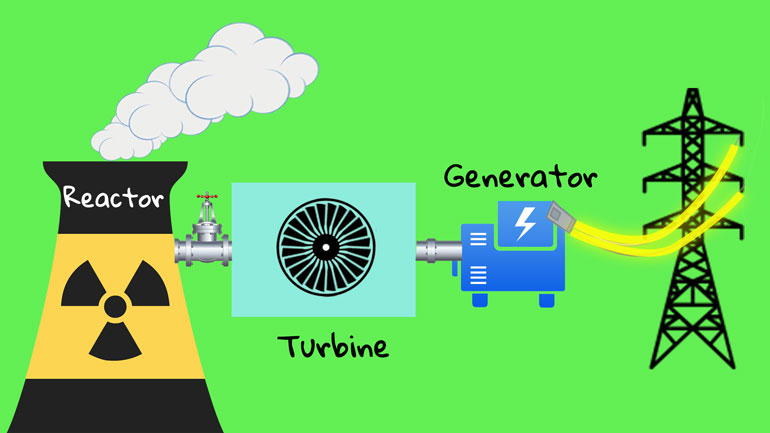
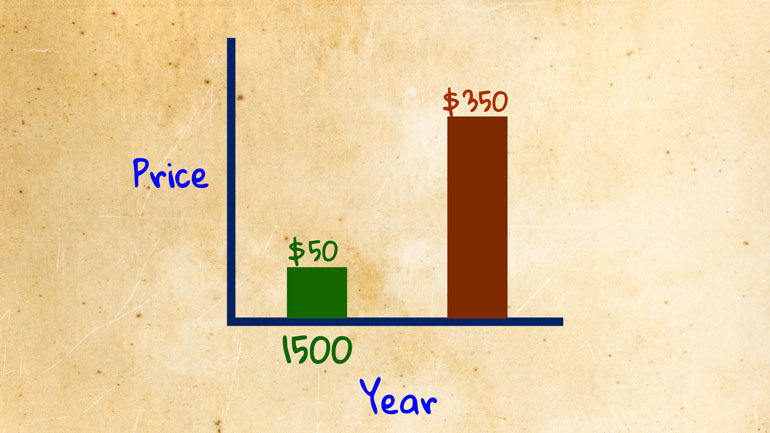
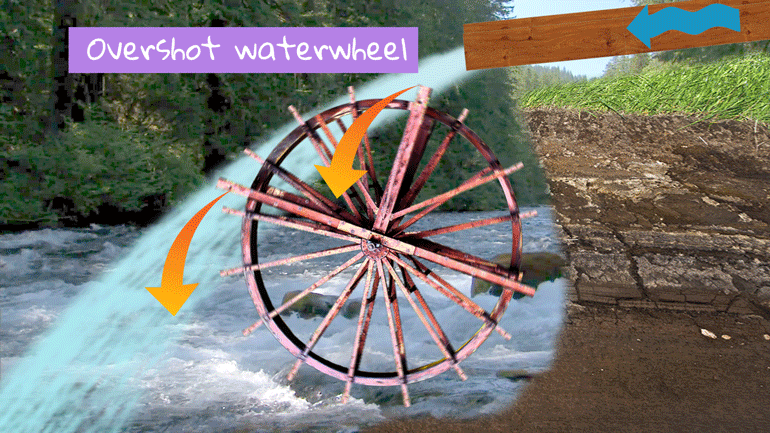
ShmoopTube
Where Monty Python meets your 10th grade teacher.
Search Thousands of Shmoop Videos
Technology Videos 160 videos
What's the deal with wind? And why does it have to be so...windy?
How did people move stuff around before the wheel was invented? More importantly, why didn't they take a break for a few minutes from moving stuff...
History of Technology 4: Cyber Warfare 5 Views
Share It!
Description:
Cyber warfare sounds scary, but guess what? ...It actually is. Sorry, we thought we could be reassuring, but then we remembered how afraid we are. ...Nothing to see here.
Transcript
- 00:00
cyberwarfare sounds like something straight out of Star Trek but actually
- 00:06
[battleships firing near earth] it's very real and it's way bigger than you might think international political
- 00:10
power games controversial secret operation cyberattacks on banks and
- 00:16
governments yep it's all happening so what if cyber war look like today where
- 00:20
do we stand well if the government can't stop kids from illegally downloading [little boy using a macbook]
Full Transcript
- 00:24
movies how will they stop cyber attacks short
- 00:27
answer well they won't cue the creepy intro music from the
- 00:31
Twilight Zone we don't want to be alarmist here cyber war probably isn't
- 00:36
going to blackout the country in the next three weeks [big red cross through planet earth]
- 00:38
plenty of people actually think what the danger of cyber attacks have been
- 00:42
overhyped some say the damage of malware and worms is nothing compared to a real [troops jumping off the back of a wagon]
- 00:47
hot war and its true that cyber war has indirectly led to killing
- 00:51
at least not yet cyber war is actually a war of information
- 00:54
it's about controlling and limiting and propagating information for political
- 00:59
[men fighting in a war] ends we'll hear a few more ways to change the rules of war now first off
- 01:04
it's nearly impossible to trace the original source of an attack unless the
- 01:08
hacker is a bumbling oaf or is just being lazy [hacker sleeping by a laptop]
- 01:11
reality check and this is hardly ever the case for attackers the other problem
- 01:16
is that if the hack is traced it's more likely to be a loosely organization
- 01:21
than a specific government entity in fact there's a whole group of hackers
- 01:25
[person typing on a laptop keyboard] out there called anonymous who have released private information for
- 01:29
political ends and crashed government websites just for kicks but nobody can
- 01:33
find them or stop them we make some crack about them but well they're
- 01:37
probably listening we love you guys no seriously we do well another huge issue [explosion in a wasteland]
- 01:41
is that attacks outpaced defense generally speaking the tech and know how
- 01:46
to attack other systems is further along than the defense systems are right now
- 01:50
[a man frantically running around a man dressed in a suit] as government's get serious about cyber defenses spending though and starting to
- 01:54
change blood-cell governments having a hard time keeping up with the nebulous
- 01:58
Anonymous group of other people to work privately on this stuff they're usually
- 02:01
[a snail moving slowly on a tree] snail pace isn't going to cut it any more government yeah want an example all
- 02:05
right well in 2012 the US government shut down a site that hosted illegals
- 02:09
torrents Anonymous launched DOS attacks on
- 02:13
government sites in retaliation and tanked a bunch of sites including [department of justice flag]
- 02:17
the FBI's website mom heres a baller for you how about another example of 2013
- 02:23
private Chinese hacker companies nabbed a bunch of top-secret weapons plans from [blueprints of a top secret rocket]
- 02:27
US government not good not good at all cyberspace is what's called the fifth
- 02:33
theater for war there used to be four theaters for war land sea air and space
- 02:38
[person typing on an electronic tablet] but now there's the entire internet and all the information we pour into it
- 02:43
every day how about WikiLeaks the site that publishes confidential government
- 02:47
and corporate information well they've released information about
- 02:51
everything from Iraqi civilian deaths to Kenyan government corruption the [man stood in front of a warning sign]
- 02:56
conditions at Guantanamo Bay while all these releases might not have killed
- 03:00
anybody yet but they sure stirred up global politics unlike a bowl of
- 03:05
porridge global politics is sometimes best left unstirred [a steaming bowl of porridge]
Related Videos
GED Social Studies 1.1 Civics and Government
When you're about to marry the love of your life, not many things could stop you. However, finding out that your future hubby is keeping his crazy...
Here at Shmoop, we work for kids, not just the bottom line. Founded by David Siminoff and his wife Ellen Siminoff, Shmoop was originally conceived...
ACT Math: Elementary Algebra Drill 4, Problem 5. What is the solution to the problem shown?